This permits them to act quickly in lieu of getting to return and try to find the link in the middle of the sentence somewhere.I concur using this fully, alas the effects of my break up assessments never. I operate Google Optimizer on each my shopper’s and my own websites – right after transforming a button from “Purchase” to “Click Here
The Definitive Guide to personal cyber security audit
Bot attacks: Automated software program applications that perform repetitive jobs, which can be applied maliciously to interact with network programs in an make an effort to compromise them or simulate fake consumer routines.An extensive analysis provides the business with a clear photograph of its techniques and ideas on how to successfully deal w
 Ralph Macchio Then & Now!
Ralph Macchio Then & Now! Michael J. Fox Then & Now!
Michael J. Fox Then & Now! Elin Nordegren Then & Now!
Elin Nordegren Then & Now!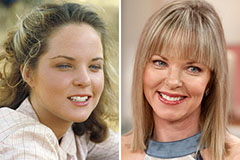 Melissa Sue Anderson Then & Now!
Melissa Sue Anderson Then & Now! Tina Louise Then & Now!
Tina Louise Then & Now!